Linux VPS servers are much more secure than other operating systems like Windows, due to the Linux security model (LSM). But they’re not flawless, and they’re certainly not invulnerable. How to secure Linux VPS and defend it against hackers?
Taking charge of your own Linux server is an opportunity to try out new stuff and maximize the strength and versatility of a great platform. However, Linux server administrators must take the same care as is necessary for any network-connected computer to keep it safe and secure.
Vulnerabilities in the infrastructure of web servers can be catastrophic. Millions of hackers around the world are working around the clock to discover even the slightest security flaws in your Linux VPS.
It’s important that you have a secure VPS against future threats because, sooner or later, the hackers will come to get you. In particular, organizational and e-commerce websites are becoming prime targets for hackers. While most businesses have basic security measures in place, they are often ineffective and easily damaged.
This post will introduce basic Linux server security to you. Although it concentrates on Debian/Ubuntu, you can extend anything presented here to other Linux distributions.
 Linux Hosting Simplified
Linux Hosting Simplified
Want a better way to host your websites and web apps? Developing something new? Simply don’t like Windows? That’s why we have Linux VPS.
Get your Linux VPSWhat is Linux VPS?
Nowadays, Linux VPS servers use cloud platforms that have better security features compared to most of their rivals. Storing data in a cloud-based environment such as a Virtual Private Server (VPS) is a very important thing nowadays to protect sensitive files. Storing data in a cloud refers to storing files elsewhere instead of storing them on a personal computer or hard drive.
But it still has its vulnerabilities that allow attackers to compromise unsecured VPS servers to steal sensitive data hosted inside them. When users order VPS hosting, an operating system is pre-installed or distributed. In any case, it is up to you to protect your VPS and select the best Linux VPS cloud.
The primary concern is to get your applications up and running in the VPS infrastructure while making your applications operate properly without any security vulnerabilities is another big concern.
Also Read: Best Linux VPS in 2022
Why You Should Secure Your Linux VPS?
At a high level, when a computer, like a server, is in the public domain and open to the outside world, it becomes a target for bad actors. An unsecured computer is a gateway for bad players who want to access your data or use your server as another node for their large-scale DDOS attacks.
The worse issue is that without good encryption, you can never know if your server has been compromised. A bad actor could have obtained unauthorized access to your server and copied your data without modifying anything and you would never know about it. Or maybe your server was part of a DDOS attack, and you wouldn’t realize that.
You can see big data breaches in the news and companies often did not discover data leakage or violation until long after the bad actors were gone.
Contrary to common opinion, bad actors don’t always try to change something or lock you out of your data for money. Often, they only want the data on your server to be stored in their database systems (there’s lots of money in big data) or to secretly use your server for their purposes.
Also Read: Test disk speed in Linux
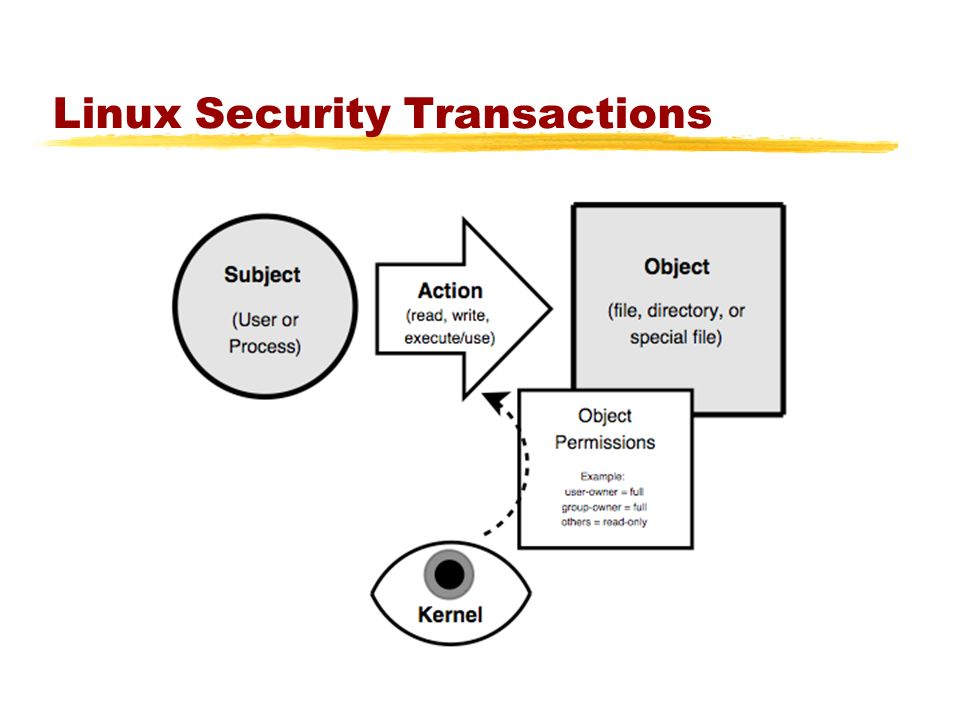
Linux Security Model (LSM)
The LSM is a code built directly into the Linux kernel that can deny process access to important kernel objects via using the LSM system. Protected object types include files, task structures, credentials, and inter-process communication items.
Manipulating these items is the primary way in which processes communicate with their environment, and by carefully defining permitted interactions, a security administrator can make it more difficult for an attacker to use a vulnerability in one program and access to other areas of the system.
LSMs are not meant to prevent a system from being attacked. Good coding standards, configuration management, and memory-safe languages are the tools for it. However, the security offered by LSMs helps to prevent your device from being hacked when an attacker exploits the vulnerabilities in one of the running programs.
It can be an important layer in every in-depth defensive strategy on Linux systems and by knowing what protections they offer, you have a better appreciation of what systems need to be protected and how to apply those protections. Linux VPS servers are much more secure than other operating systems like Windows due to the Linux security model (LSM).
 Linux Hosting Simplified
Linux Hosting Simplified
Want a better way to host your websites and web apps? Developing something new? Simply don’t like Windows? That’s why we have Linux VPS.
Get your Linux VPS20 Ways to Secure Linux VPS
In this section, we have listed the top 20 ways that you can read to realize how to secure VPS Server with a Linux operating system. You may have already heard that Linux is a secure operating system but this fact should not keep you away from taking the necessary steps to secure Linux VPS.
Alo Read:
1. Keep the Software Up to Date
You should keep an eye on software updates in your server software by using the RMP package manager or YUM package manager (CentOS/RHEL) or apt-get (Ubuntu/Debian) and download the latest version of the software and component updates.
You also need to focus on panels such as Plesk or cPanel and review notifications if they are not updated automatically. You can also configure your operating system to send reminders of yum package updates via email.
2. Disable the Root Login
You should never sign in as a root client. As a general rule, every Linux server has “root” as a username, so hackers are trying brute force attacks to crack the password and gain access.
Disable logins from the root username includes another layer of protection since it stops attackers from guessing the hidden passwords.
Develop a new username and use the Sudo command to run root-level commands instead of logging in as a root user. Sudo gives special access to approved users that helps to run administrative commands without root access authorization.
Before you disable the root account, make sure that your non-root user is generated and that the required level permissions are provided.
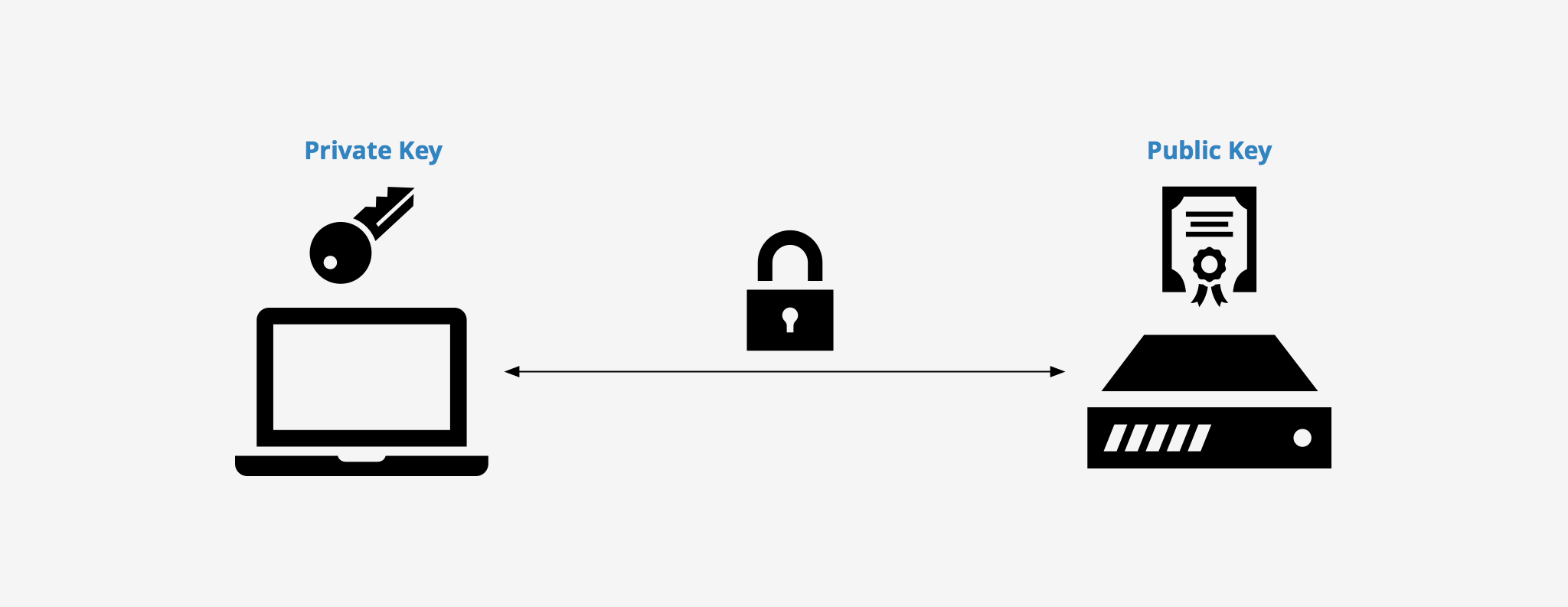
3. Generate an SSH Key Pair
Although strong passwords can make a difference, even better methods for logging in to private servers are possible. In particular, Secure Shell (SSH) key pairs are worth introducing since these systems are much more difficult to hack via brute force.
Before using SSH keys, it is necessary to understand why you’d want to implement them instead of the regular username and password setup. Although passwords are more convenient for day-to-day users, these same users tend to rely on easily guessed choices that leave the whole security infrastructure unprotected.
SSH key pairs are not as user-friendly as passwords, but they are considerably more secure. This improved security can be related to the encryption used by both the server you log into and the device you use.
At a minimum, the SSH key pair is equal to a 12-character password, however, the vast majority of key SSH pairs are much more complicated. For this reason, SSH key pairs should be one of the first steps to be introduced when implementing a proactive server security strategy.
4. Enable Two-Factor Password Authentication
Check the strength of the password that you use for the cloud accounts and enforce the minimum password implementation policy. Never use the same password for different resources, get a password manager, and set unique passwords for each service.
Enable minimum two-factor authentication to preserve data and protect your account. Ensure that you will be told if someone is trying to reset your secret key, and if security problems are included, make sure you pick deep questions.
5. Change the SSH Port
It is rather hard for hackers to hack SSH because they can’t find it. Changing the SSH port number will prevent malicious scripts from connecting directly to the default port (22).
To do this, you’re going to need to open
/etc/ssh/sshd_config
and change the appropriate settings. Double-check whether any other services use the chosen port number
6. Disable Unused Network Ports; Disable IPv6
Cybercriminals primarily target open network ports and unused network services, and you’ll need to protect yourself from misuse. Use the “netstat” command to view all currently open network ports and their related services.
Hackers who often send malicious traffic via IPv6 and leave the protocol open can expose you to potential attacks. IPv6 has some advantages over IPV4, but it is used by a smaller group of users.
Use “iptables” to close all open ports or use the “chkconfig” command to disable unnecessary services.
Also Read: Enable/Disable IPV6 on Ubuntu
7. Configure a Firewall
To filter out unnecessary traffic on your VPS server, you need a firewall to combat distributed denial of service (DDoS) attacks. Popular firewalls, including CSF and APF, provide plugins for popular panels such as cPanel and Plesk.
Installing and Configuring a Firewall should be one of the first things you do when you set up a new Linux VPS. Use SFTP, which is “FTP over SSH” instead of a File Transfer Protocol (FTP) that is obsolete and no longer secure.
 Linux Hosting Simplified
Linux Hosting Simplified
Want a better way to host your websites and web apps? Developing something new? Simply don’t like Windows? That’s why we have Linux VPS.
Get your Linux VPS8. Install anti-malware and anti-virus applications
The key task of a firewall is to prevent access to any known source of malicious traffic, and it essentially serves as your first line of protection. But no firewall is flawless and malicious applications can still slip through, which is why you need to defend yourself further. Too many inexperienced server administrators have neglected to install anti-malware apps.
The most common explanation for this is not ignorance. It’s because they don’t want to spend money on security products. As a principle, pay-as-you-go options are generally the best because their revenue stream helps them to recruit skilled programmers and researchers who can help the app remain relevant.
Also Read: Best Linux Mail Server Antivirus 2022
9. Install a rootkit scanner
One of the most dangerous malware pieces is the rootkit. It resides at the level of the operating system (OS), below other standard security software, and can allow undetected access to the server.
Luckily, you can use tools like Chrootkit, an open-source scanner, to find out if your server is affected. But rootkits are not always easy to uninstall, and the easiest way to address the problem is always to reinstall the operating system.
10. Choose a Secure Physical System
The current VPS system is a very stable one. However, they are vulnerable to some forms of security problems that are not faced by other systems. Typically, this is not a concern for most users.
A successful VPS provider should take all required security requirements to maintain the physical security of the device. This will include limited access to the metal devices themselves.
Note, however, that a VPS provider cannot have a certain level of protection by definition. For example, anything that needs to be air-gapped can’t go to a VPS. National security networks are another example of something that can’t go on a VPS.
Also Read: 5 ways to Secure Windows VPS
11. Turn on SELinux
SELinux is a necessary security kit provided by the Linux Foundation. SELinux is easy to install and comes pre-installed with every Linux distro. If you want a secure VPS, make sure that SELinux is always on.
Of course, merely turning SELinux on is not enough to secure your server. Follow these short instructions to get the most out of SELinux.
You can check the status of your daemon by using the following command:
# sestatus
If it’s off, you can turn it on with this command:
# setenforce enforcing
12. Protect Files, Directories, and Emails
Linux provides excellent protection against unauthorized access to data. However, Linux permissions are meaningless if an attacker has physical access to a device and can easily transfer a computer’s hard drive to another machine to copy and review sensitive data.
Use the “gpg command” to encrypt and decrypt files with a password. Linux or UNIX password lock files with OpenSSL and other methods.
Complete disk encryption is a must for data protection and is supported by most Linux distributions. Also, make sure that the root mail is forwarded to the account you check.
 Linux Hosting Simplified
Linux Hosting Simplified
Want a better way to host your websites and web apps? Developing something new? Simply don’t like Windows? That’s why we have Linux VPS.
Get your Linux VPS13. Take Backups Regularly
Too many users fail to take backups on a regular basis, and then they regret it when something unexpected happens and they don’t have a copy of their data. No matter how cautious you are, and no matter how safe your server is, there’s always a risk that something could go wrong.
Don’t take unnecessary risks by failing to take backups, and don’t rely on your host to do so either. It is recommended that you take your own backups, even though your hosting company claims they do it on your behalf. Keep copies in various places and try using the cloud so that your copy can be accessed from anywhere.
14. Create disk partitioning
Disk partitioning is one of the smartest tools to increase your Linux VPS security. Using this method gives you a chance to separate valuable system files from different types of files to cut down the corruption risk.
For instance, assign a dedicated system space, applications, and data for particular uses in different partitions help you to prevent missing the data when it comes to corruption or attacks.
Based on this fact, running multiple operating systems in several partitions is a great solution for vulnerability growth. In addition, it can optimize your system security when you disable SUID/SGID access (nosuid) and the execution of binaries (noexec).
15. Remove unwanted modules and packages
The other powerful method that is crucial to running a secure Linux VPS is to use the required services you need and want. Removing unused and useless packages makes a significant impression on your system performance. It offers valuable advantages such as increasing the disk space, optimizing extra resources and maximizing the binaries’ security.
These commands can remove unwanted packages
yum list installed
yum list packagename
yum remove packagename
16. Use GnuPG encryption
It is absolutely essential to take advantage of high-security password protocol to keep your critical data safe and secure. GnuPG encryption is an efficient tool that allows users to use a unique personal key for data encryption, decryption, and sign communication.
It also takes control of the data ownership and security against modification and tampering. This strong password encryption built a key-based authentication that avoids hackers’ attacks and provides good privacy by public and private keys to encrypt and decrypt messages.
The public key lets senders encrypt the data message and send it on the network; then receiver uses the private key to decrypt and read it. After that, we can create a message through the primary sender’s public key to encrypt the message and send it back. In response, they should use the private key to decrypt and read the message.
17. Prefer SFTP over FTP
SFTP is the most secure file transfer protocol that guarantees data protection and privacy using SSH. However, FTP is a non-security file transfer protocol that hackers can easily access and decrease your vulnerability to hackers’ brute force attacks or spoofing attacks.
Using FTP won’t offer fast delivery and encrypted transmitting files. It is possible to establish a secure connection, but the content of files is not encrypted. Therefore, exchanging sensitive data needs authentication by the server, SFTP makes the connections encrypted, and the file transfer process is more reliable and secure. That is why we preferred SFTP over FTP.
18. Enable CMS auto-updates
Keep in mind that Content management systems (CMS) need updating to install security patches to avoid website hacks and attacks. As they are open-source software, it is the fundamental task to secure your Linux system by simply auto-updating your CMS.
No difference whether you use Joomla, WordPress, or drupal; you have to do continuous security updates to immune security risks like loss of data and sensitive information. So it’s essential to use rolled-out CMS security fixes and new features for Linux VPS security growth.
- Automatic updates let your CMS core, themes, and plugins are updated with the latest virus definitions and maximize your website security from potential future attacks.
- It eases the process of managing multiple different websites for Website owners when the number of websites increases
- Find the latest features and fixes bugs from the previous version that impact the performance and stability.
19. Disable anonymous FTP uploads
Anonymous FTP lets unprotected remote accesses to the FTP server without any credential (User Id and Password). Web hosting control panels includes cPanel, and Plesk closes anonymous FTP uploads by disabling write access for that user. FTP data transition is vulnerable to sniffing, spoofing, and brute force attacks, among other attack methods, puts you at risk of massive security.
- Log into your cPanel.
- In the Files section, select the Anonymous FTP icon.
- Under Anonymous FTP Controls, uncheck both boxes “Allow anonymous access” and “Allow anonymous uploads.“
- Click Save Settings.
After completing these steps, you can still see [email protected] and [email protected] listed in your cPanel FTP accounts, but they are not enabled.
20. Configure cPHulk in WHM
WHM/cPanel released with a built-in firewall called “cpHulk.” It is one of the most common ways to penetrate your web services brute force attacks. Malware or malicious software can break into your authentication system by frequent login attempts, and fortunately, cPanel includes “cPHulk” for brute force protection.
It means that cPHulk closes up the login ability first and that the firewall later gets going. The configuration process is a piece of cake in compression to security software that needs a command-line interface. To protect your Dedicated Linux VPS hosting from brute-force attacks, you need to root access to enable cPHulk.
- Log in to WHM as the root user.
- Search the “Security “in the search box
- Click the Security Center link.
- On the Security Center page, click the cPHulk Brute Force Protection button.
- After that, you can see that cPHulk is disabled.
- toggle it on in the menu to enable it
- when toggling it on, choose the cPHulk settings you want,
- Click the Save button
 Linux Hosting Simplified
Linux Hosting Simplified
Want a better way to host your websites and web apps? Developing something new? Simply don’t like Windows? That’s why we have Linux VPS.
Get your Linux VPSConclusion
This guide provides the minimum needed to secure a Linux VPS server. Additional security layers can and should be activated depending on how the server is used. These layers can include such items as individual application configurations, intrusion detection software, and access controls. There are several different security concerns that come under the general category of Linux security, and there are many theories as to what an acceptable level of security looks like for a Linux server.
The key takeaway from this guide is that you will have to determine for yourself what security measures are required. Before that, you should be aware of the risks and difficult choices and settle on the balance between usability and protection that makes sense to you. The need for a secure payment system becomes more apparent when you need a global service like VPS, therefore we offer VPS with crypto payment for securing your payment.












Thank you for this comprehensive article, in my opinion the most important measure in a Linux VPS security is the vps provider. I mean their infrastructure and security model should be really powerful so that the users do not face any problem
Great article! Keep up the great work
Is VPS hosting secure itself? How different is it from shared hosting or dedicated hosting?
As far as I know enabling two factor authentication and using an ssh key pair is really helpful 🙂
I recommend everyone with this concern to set up SELinux, it won’t do any harm to just try it.