I’m going to depict a very childish fantasy that we all shared as kids. Imagine you have a pair of magical glasses that let you find hidden treasures in a library. It’s a new visionary experience. These magical glasses allow you to see the invisible, the unnoticeable. Now, imagine having this superpower to discover hidden content on the Internet. Imagine having special secret words that help these magical glasses work even better. These secret words help you find very specific things, like hidden treasures, that you wouldn’t find just by looking around normally. You can’t argue that this isn’t the coolest superpower ever. Like, who wants to fly when you can see the rarest pieces of content, right?
If you’re curious to learn more about this superpower, welcome to Google Dorking! In this blog post, we’ll learn how to access the hidden corners of the Internet.
What Is Google Dorking?
Google Dorking involves using advanced search syntax in Google to find specific information that is publicly available on the internet. These specific pieces of content are available but not on the surface; accessing them requires a little bit of digging. Google Dorking does this digging by using special operators and commands that refine search queries. This means users can locate sensitive information, detect security vulnerabilities, and gather data that might not be easily found through regular searches.
Operators like site:, filetype:, and inurl: are used to narrow down search results to specific websites, file types, or URLs. For instance, using site:example.com filetype:pdf would return PDF files hosted on example.com. Google Dorking can uncover directories, confidential documents, and detailed error messages that reveal weaknesses in a website’s security.
Use Cases for Google Dorking
Google Dorking is not just a tool for curious people. It’s a powerful asset that can be used in many professional and educational scenarios. Here are some of the most common use cases for Google Dorking:
Security Assessments and Vulnerability Testing
So, as I explained earlier, Google Dorking commands can find information that’s typically out of reach. Now, imagine you have mistakenly published confidential data. What if someone uses Google Dorking commands to uncover this exposed information? The solution here is that you take action first and employ Google Dorking commands to find vulnerabilities within your system.

Competitive Intelligence Gathering
If you’re a business developer or marketing specialist, having up-to-date knowledge is one of your important superpowers. Google Dorking gives you the opportunity to gather competitive intelligence. Marketers and business analysts use Google Dorking to find information on competitors’ website structures, online strategies, and publicly accessible documents that may reveal strategic plans or new product launches. You can use this insight to benchmark the performance of your company, anticipate market moves, and develop counter-strategies.
Academic Research and Data Collection
If you’re a researcher or an academic professional, Google Dorking can help you refine your search queries and extract precise datasets from the vast sea of online information. The ability to find research papers, datasets, case studies, and articles that are not easily accessible through standard search methods can accelerate your research process. And what matters more than efficiency and speed for a Ph.D. student with strict deadlines?
Locating Software and System Vulnerabilities
If you’re an ethical hacker or penetration tester who wants to identify software vulnerabilities and misconfigurations, Google Dorking can make this process more efficient for you. Google Dorking allows you to craft specialized queries. You can then use these queries to locate systems running specific software versions known to be vulnerable, misconfigured network devices, or exposed administrative interfaces. This type of identification allows for the timely patching of vulnerabilities and the strengthening of system security postures against potential attacks.
Finding Unauthorized Copies of Copyrighted Material
If you’re a copyright holder or content creator, you can use Google Dorking to find unauthorized reproductions of your work. Through specific search commands, you can locate websites hosting pirated copies of books, music, movies, and software. This aspect of Google dorking helps with protecting intellectual property and taking legal action against copyright infringement.
I understand that many of these use cases are dedicated to a specific group of people. However, you can also use Google Dorking for daily purposes. Even if you’re a normal Internet user curious about the depth of the Internet, Google Dorking can enhance your search experience.
Google Dorking Commands and Examples
Google Dorking can find search results that you’ll never get from standard search queries. And it does that by implementing advanced search operators. These search operators work by implementing a new approach to tell Google’s search algorithm what to look for. Now, let’s see what these search operators are capable of doing:
Inurl: This search operator is able to find specific keywords in a URL. For example, ‘inurl:admin’ will return pages that have “admin” in the URL.
Filetype: The filetype operator would return all the files with the specific file type you had asked for. For example, ‘filetype:pdf site:example.com’ will look for PDF files within the example.com domain.
Intext: This search operator looks for specific words or phrases in the content of a web page. ‘intext:”confidential” filetype:pdf’ looks for PDFs containing the word “confidential.”
Link: If you want to know what pages link to a specific URL, you can search the URL with the link search operator. For example, ‘Link: https://example.com/webpage’ shows which pages link to a specific article on your website.
Site: This site operator restricts the search results and only shows the results from a specific website. For example, ‘site:example.com’ will return web pages only from example.com.
Intitle: The intitle operator searches for pages with specific words in their titles. For example, ‘intitle:”index of” “password”’ helps find pages that might list passwords.
Cache: This operator displays Google’s cached version of a web page. For example, ‘cache:example.com’ shows the most recent cached page of ‘example.com’ by Google.
Google Dorking Examples in Action
In order to provide more depth to our Google Dorking conversation, I want to add details to two of these operators. The first handy Google Dorking command is ‘site: ’. Have you ever wished you could filter the entire internet to find content from one website?
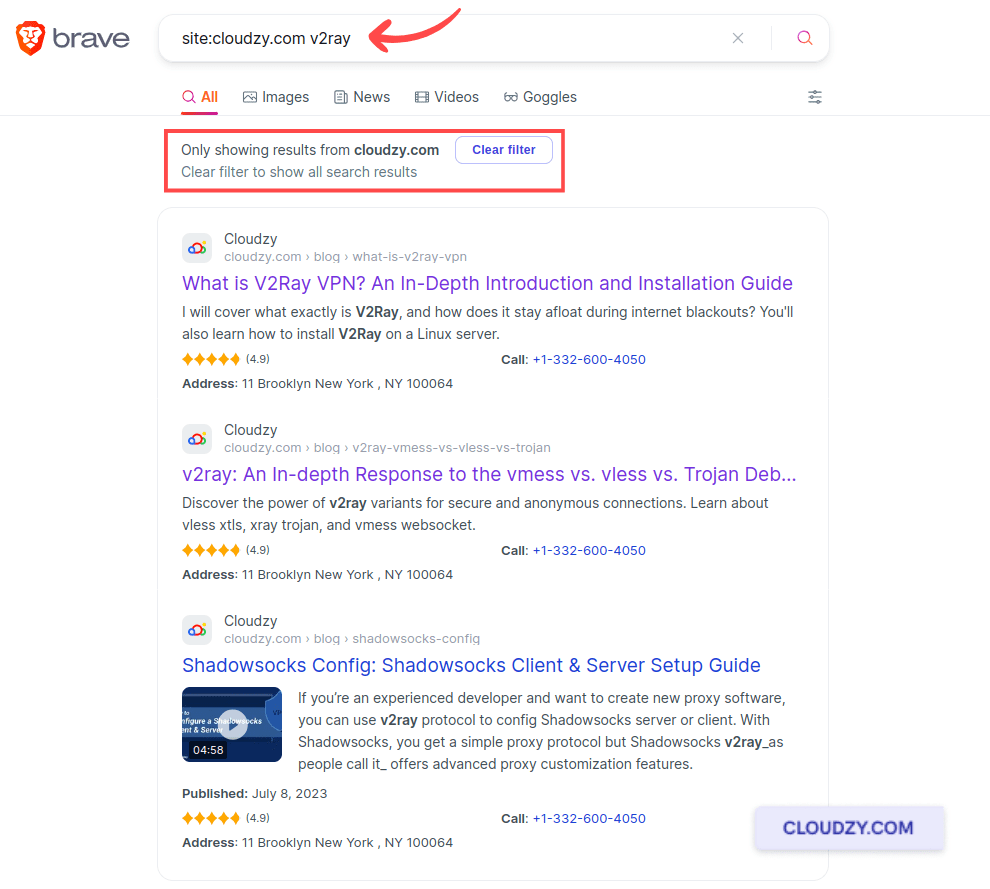
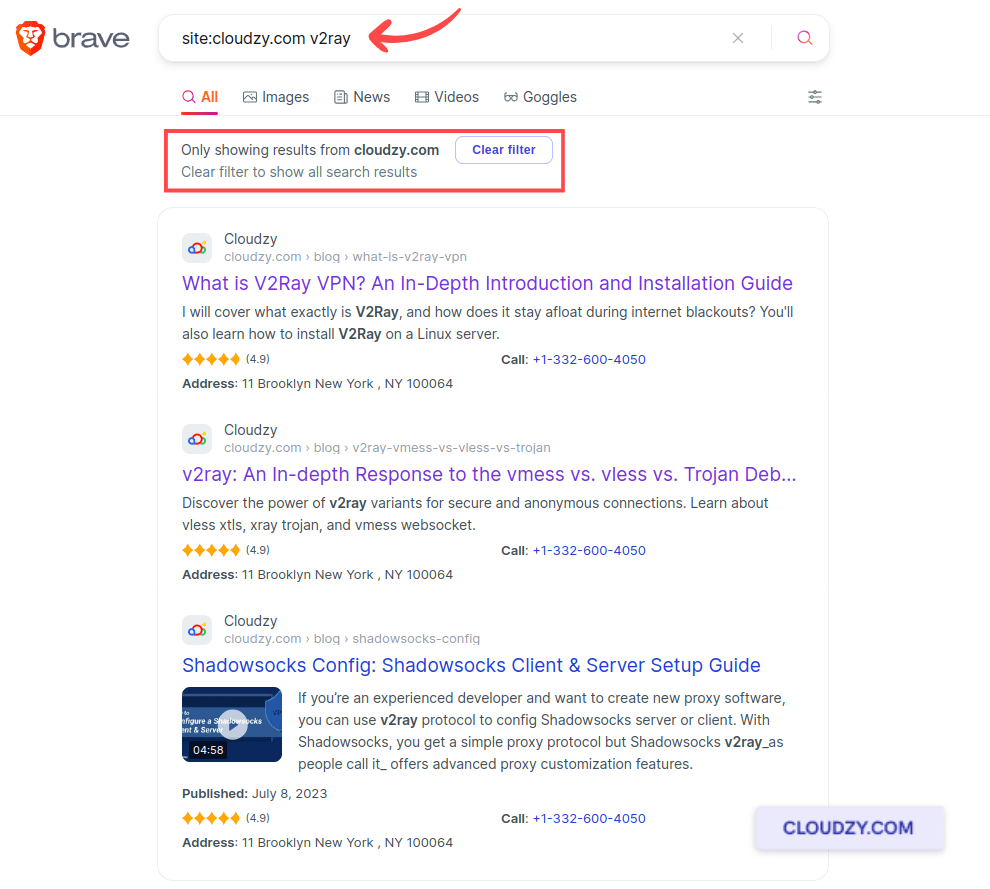
The site operator focuses on a specific domain and allows you to sift through a single website’s content directly from Google’s search bar. Imagine you’re looking for all the blogs about V2Ray on Cloudzy’s website. All you have to do is type ‘site:cloudzy.com v2ray’. This query returns all pages about V2ray on Cloudzy.
The next helpful Google Dorking command that I want to explain in detail is the ‘filetype: ’ operator. If you’re digging for specific document types, the filetype: operator can be really helpful. Whether you’re looking for PDFs, PPTs, or spreadsheets, this operator filters search results to show only the file types you need. You’re on the hunt for research papers on renewable energy. Instead of wading through web pages, you’re interested in direct sources, preferably in PDF format. Here’s how you could use Google:
As you can see in this example, every result on this page is a PDF file. This way, it’s way easier for you to find scholarly articles, reports, and papers.
Now that we’ve reviewed all the important google dorking commands and made two practical examples, let’s move on to the next section to learn how to protect our data against google dork commands.
How to Protect Your Digital Assets from Google Dorking
The Internet age has some characteristics that act as a double-edged sword. For example, the Internet allows information to flow like water and seep into every corner. In most cases, this is a positive feature that makes information accessible to everyone. But in some cases, it can be tricky. As soon as you put something online, you should expect all sorts of malicious activity and exploitation. Although Google Dorking is a powerful tool for cybersecurity professionals and researchers, it also has significant risks when used by a malicious actor. In this section, you’ll learn how to secure your information and protect it against malicious Google Dorking attempts.
1. Regularly Update and Patch Systems
Hackers often use Google Dorking commands to find exploitable targets that are running outdated software. One of the most effective ways to secure your systems against Google Dorking is to keep your software and systems up to date. So, make sure you apply security patches and updates as soon as they become available to minimize risks.
2. Strengthen Web Server Configurations
Web servers that are not properly configured are easy targets for Google Dorking. If you want to protect your digital assets, you need to make sure that your server configurations do not expose sensitive information. One way to do this is by disabling directory listings and ensuring that files such as .git or backup.zip are not accessible via the web. Also, regularly consult the Google Hacking Database to learn about new potential exposures and how to secure them against Google Dorking techniques.
3. Monitor and Analyze Web Logs
Monitoring your web logs can help you detect potential Dorking activity. Look for unusual patterns or an increased number of requests that involve Google dork commands. If you do this monitoring regularly, you can detect these activities and prevent data breaches.
4. Use of Robots.txt and Web Application Firewalls
In order to explain Robots.txt, we need to dive into a familiar scenario. Imagine you take your favorite sandwich to the office. To make sure your colleagues don’t touch our heavenly sandwich, you put a sign on it that says “Do NOT Touch!”. This sign is like a robots.txt file on a website. It tells search engines like Google not to show certain parts of your website in search results. But what if that one annoying colleague who’s entitled enough to eat your sandwich, ignores the sign? Just like this scenario some sneaky internet users can ignore the robots.txt sign and try to find hidden stuff on a website. Now, think about having a superhero guard named WAF (Web Application Firewall) who watches over your toy box. Even if someone ignores the sign and tries to peek, the superhero steps in and stops them. So, pairing Robots.txt and Web Application Firewalls is a great strategy detect and block exploitation attempts that use Google hacking.
These steps allow you to protect your digital assets from Google Dorking threats. Regularly revisiting and updating your security measures in line with the latest developments in the Google Hacking Database will help keep your defenses strong and resilient.
Google Dorking Cheat Sheet
This Google dorks cheat sheet provides a reference to some of the most effective Google Dorking commands. You can use this table to easily find Google dork commands.
| Command | Purpose | Example |
| site: | Searches for specific content within a particular website. | site:example.com |
| filetype: | Looks for files of a specific type. | filetype:pdf |
| intitle: | Finds pages that include specific words in their titles. | intitle:”login page” |
| inurl: | Searches for URLs that contain a particular word. | inurl:”admin” |
| cache: | Shows the cached version of a webpage. | cache:example.com |
| info: | Provides summary information about a site. | info:example.com |
| related: | Finds websites related to the specified site. | related:example.com |
| intext: | Looks for text anywhere in a webpage. | intext:”confidential” |
Tips for Using This Google Dorking Cheat Sheet:
- Combine Commands: You can increase the precision of your searches by combining commands. For example, using site: together with filetype: can help pinpoint specific documents.
- Regular Checks: Use these commands regularly to scan your own websites for exposures or accidental information leaks.
- Stay Updated: As new commands are developed and shared within the Google Hacking Database (GHDB), keep your cheat sheet updated to include these advancements.
Get yourself an economy or premium Linux VPS for hosting your website or remote desktop, at the cheapest price out there. VPS Running on Linux KVM for increased efficiency and working on powerful hardware with NVMe SSD storage for increased speed.
Read MoreConclusion
Learning Google Dorking has lots of benefits and use cases. You can use it to enhance your cyber security measure, or you can use it to find valuable information online. Always remember to use these powerful tools responsibly and ethically. Although Google Dorking is not illegal, you should watch how you use it due to ethical measures.
FAQ
What are the benefits of Google Dorks?
Google Dorks help refine searches to find specific information quickly. This allows cybersecurity professionals to safeguard systems more effectively. Additionally, Google Dorks are great for research because they can provide precise data that can be used for competitive intelligence or academic purposes.
What is Google hacking database?
The Google Hacking Database (GHDB) is a repository of Google dorking commands that are used to find security holes in websites and servers. It serves as a resource for security professionals to understand and anticipate the methods hackers might use to exploit vulnerabilities found through Google searches.