Move fast, pay only for what you use, and hand patching to someone else, and that pitch still lands. Yet the honeymoon fades once runaway storage bills arrive or an overlooked S3 policy leaves a bucket wide‑open. From hard‑won experience, I see the same major challenges for cloud computing raise their heads across stacks and industries. By lining them up early, we dodge most of the pain and keep the team focused on shipping features instead of fighting fires.
Why These Headaches Refuse to Go Away
Cloud failures rarely spring from a single catastrophic bug. They snowball from small gaps that stack up across architecture, process, and people. Before we dig into each category, here is a snapshot of symptoms that show something deeper is off:
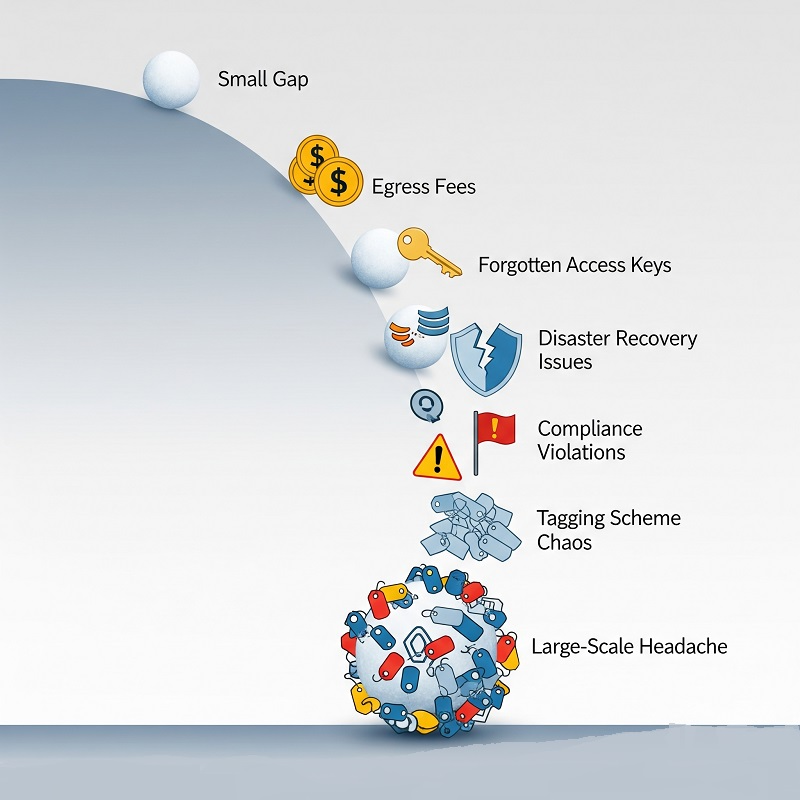
- A sudden jump in egress fees wipes out two months of margin.
- A forgotten access key fuels an overnight crypto‑mining spree.
- A region‑wide outage tests a disaster‑recovery plan nobody rehearsed.
- A compliance audit flags unlabeled sensitive data parked in object storage.
- Ten squads adopt ten tagging schemes, so charge‑back reports read like hieroglyphs.
Each symptom traces back to one or more core risk buckets. Keep that map close; it guides every mitigation step later.
Risks of Cloud Computing
Industry studies consistently point to seven core risk buckets that account for the bulk of incidents across sectors. Although these categories bleed into one another, together they map the major challenges for cloud computing teams bump into day‑to‑day, from cost blowouts to data exfiltration:
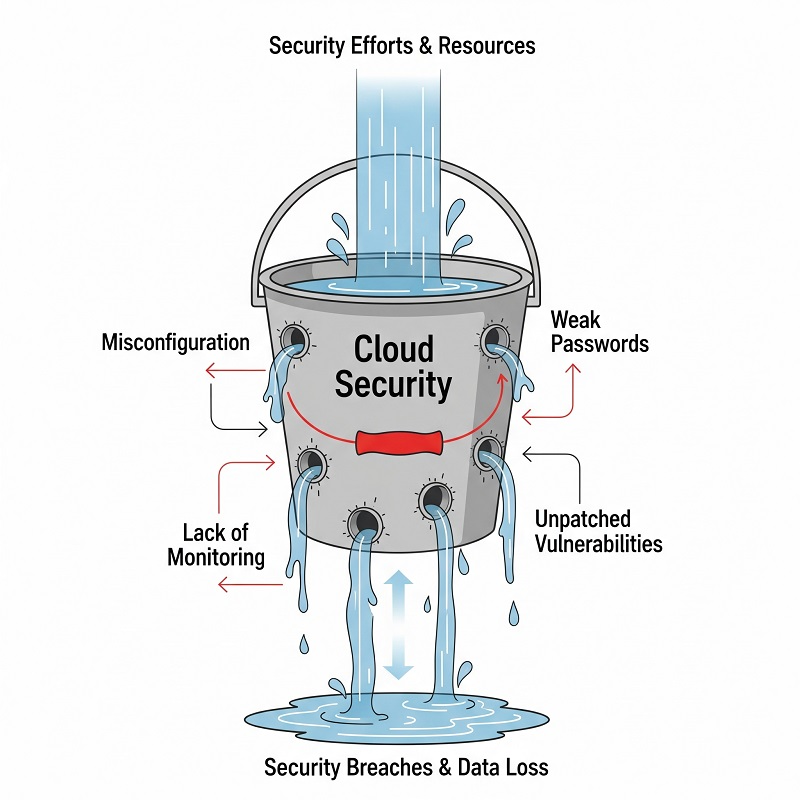
Misconfiguration & Excess Privilege
Even seasoned engineers mis‑click a console toggle now and then. An overly permissive security group or a public storage bucket turns an internal tool into an internet‑facing liability.
Common slip‑ups
- Wild‑card 0.0.0.0/0 rules on admin ports.
- IAM roles that grant full access long after a migration completes.
Data Breach & Leakage
Once misconfigurations open the door, data leaves. Data Breaches are a recurring headache in cloud security, and they rarely start with sophisticated zero‑days; they flow through exposed endpoints or stale credentials.
Insider Threat & Shadow Admins
Not every risk sits outside the company. Contract staff holding retained privileges, or employees who spin up unsanctioned services, create blind spots that standard monitoring misses.
Insecure APIs & Supply‑Chain Exposure
Every cloud‑native app leans on third‑party SDKs and APIs. Missing rate limits or unpatched libraries invite abuse, turning an innocuous feature into an attack surface.
Limited Visibility & Monitoring Gaps
If logs live in one account and alerts in another, incidents stretch on while teams scramble for context. Blind spots hide both performance drift and active intrusions.
Security Worries That Keep Teams Up at Night
The principles set out in our article on what is cloud security provide a solid baseline, yet sophisticated attackers still slip through unless companies automate log review, MFA, and least‑privilege design. Without those guardrails, the major security issues in cloud computing move from abstract to urgent. Modern Cloud security tools help shorten detection time, but only when teams wire them into daily workflow.
Key takeaways:
- Map every external endpoint; scan for unintended exposure weekly.
- Rotate keys automatically; treat long‑lived credentials as debt.
- Feed audit logs into a central SIEM, then alert on anomalies instead of raw errors.
Operational and Financial Surprises
High availability sounds simple until a multi‑AZ database cluster starts doubling your bill. Among the major challenges for cloud computing hiding in plain sight, cost drift ranks near the top. Support tickets pile up whenever instance families deprecate, or when capacity limits throttle scale‑up events.
Teams that need fine‑grained control sometimes move latency‑sensitive services to a lightweight VPS Cloud setup. By pinning workloads to guaranteed vCPUs, they sidestep noisy‑neighbor effects while keeping provider flexibility.
Common Cloud Issues on the Ops Front
- Under‑provisioned limits blocking sudden traffic spikes.
- Vendor lock‑in making data‑plane changes slow and pricey.
- Unexpected cross‑region transfer fees during failover tests.
Governance and Compliance Pitfalls
Auditors speak their own dialect, and the cloud adds fresh jargon on top. When tagging, retention, and encryption policies drift, findings multiply quickly. The table below highlights four frequent gaps I bump into during readiness reviews:
| Compliance Gap | Typical Trigger | Likelihood | Business Impact |
| Unclassified personal data stored in object storage | Missing data inventory | Medium | Fines, brand damage |
| No MFA on privileged accounts | Speed over process | High | Account takeover |
| Disaster‑recovery plan never tested | Resource pressure | Medium | Prolonged downtime |
| Proprietary features deeply embedded | Convenience at build time | Low | Costly exit, slowed migration |
Notice how each row ties back to one of our computing challenges above. Visibility, least privilege, and repeatable testing form the backbone of any successful audit cycle.
Tackling the Pain Points
No silver bullet exists, yet a layered approach chips away at risk fast. I group tactics into three buckets:
- Harden the Foundation
- Baseline every account with infrastructure‑as‑code; drift alerts catch sneaky changes.
- Enforce MFA at the identity provider level, not per application.
- Automate Detection and Response
- Centralize logs, then aggregate with resource tags so alerts explain what broke, not just where it broke.
- Spin up sandbox copies weekly to test patch sets before production sees them.
- Plan for the Inevitable
- Run game‑day scenarios: pull the plug on a service and watch dashboards swing; lessons stick better than slide decks.
- Keep a clean, portable image on standby; a one‑click Buy Cloud Server option acts as a safety valve when regions melt down.
Adopt the pieces that fit your stack first, then widen coverage. Small wins, like auto‑tagging or daily key rotation, compound over time.
Final Thoughts
Cloud adoption stays on an upward curve, so ignoring its pain points is not an option. By mapping your environment against the major challenges for cloud computing described here, you spot weak spots early, keep spend predictable, and let developers ship features with confidence. The journey never truly ends, but with clear eyes, solid tooling, and a habit of regular review, the cloud stays an accelerator rather than a source of midnight pages.
Speed, consistency, and airtight safeguarding come baked into Cloudzy’s VPS Cloud portfolio. Each instance rides on NVMe storage, high-frequency CPUs, and redundant Tier-1 routes, meaning workloads launch quickly and stay responsive even during volume surges. Enterprise-grade firewalls, isolated tenants, and continuous patching lock down the stack without slowing anything down. If you want to buy a Cloud Server that checks all the security and reliability boxes, look no further!



