Both Telnet and SSH are network protocols designed to access and manage remote systems. But how do they differ from each other, and when should we choose one over the other? In this article, we will get into the Telnet vs. SSH debate and see how they compare. Before going through the details of Telnet vs. SSH, we should know more about these protocols.
What is Telnet?
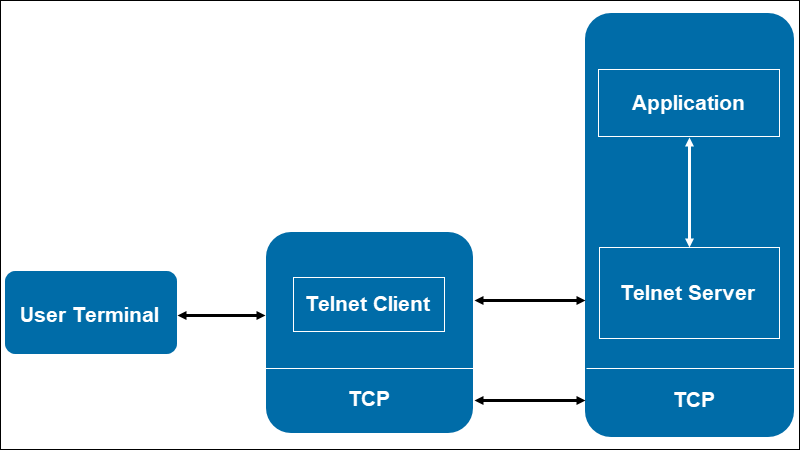
The word “Telnet” stands for Terminal Network and is practically as old as the internet. Telnet is the standard TCP/IP protocol designed for virtual terminal services. Using Telnet allows you to establish a connection to a remote system in a way that appears like a local system. In other words, Telnet is a network protocol that enables virtual access to a computer and provides a two-way, collaborative, and text-based communication channel between two systems.
- [Telnet]
What is SSH?
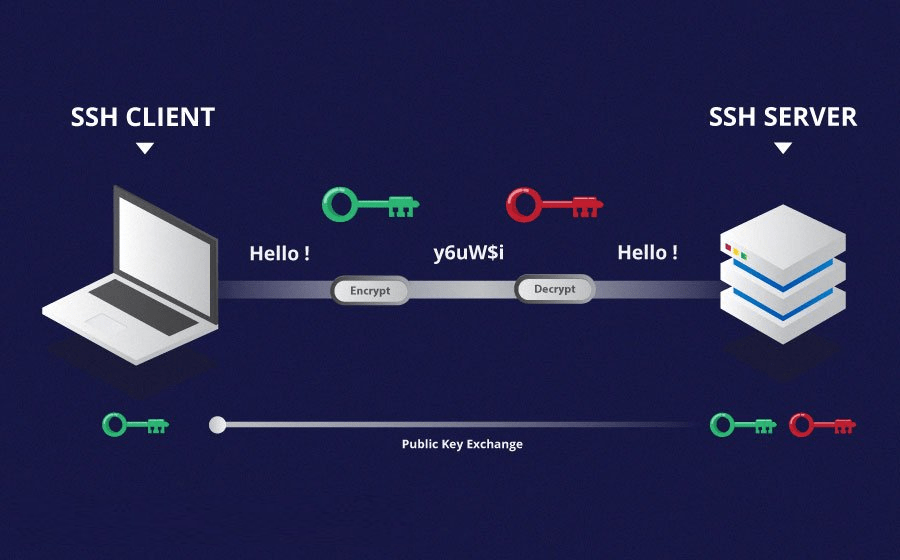
SSH (Secure Shell), also known as Secure Socket Shell, is a network protocol that offers users, especially system administrators, a secure way to access a computer over an unsecured network. Not only does SSH strong password and public key authentication, but it also gives you encrypted data communications between two computers connecting over an open network. In simple terms, SSH protocol can encrypt traffic in both directions, helping you to prevent trafficking, sniffing, password theft, and other complications.
In addition, network administrators can widely use SSH to manage different systems and applications remotely. This feature of SSH enables network administrators to log in to another computer over a network, execute commands, and move files between computers. Now that you are familiar with these protocols, we can discuss the purpose of this article (Telnet vs. SSH comparison) in the following section.
Also read: How To Use SSH to Connect to a Remote Server in Linux?
- [Telnet vs SSH]
Telnet vs SSH: what are the main differences?
Even though Telnet and SSH have some similarities, there are many differences between these protocols, which can separate them. The most significant dissimilarity between the two is that SSH is more secure than Telnet. For this reason, we can say that SSH has replaced Telnet almost in every service. Having this in mind, let’s discuss Telnet vs. SSH comparison in more detail.
Telnet vs SSH: Definition
In Telnet vs. SSH comparison, even their definitions are distinctive. Telnet is a joint abbreviation of Telecommunications and Networks, and it is a networking protocol mostly known for the UNIX platform. On the other hand, SSH or Secure Shell is a cryptographic network protocol for operating network services securely over an unsecured network. SSH assists you with logging into another computer over a network, executing commands in a remote machine, and moving files from one system to another.
Telnet vs SSH: Operation
Telnet requires a server application on the remote system so that you can manage it. It is also necessary to install the client application on the local machine. When you want to connect to with a remote system via Telnet, TCP protocol and port 23 are used to make this possible for you. After that, This system functions as a Telnet server and can receive commands. The NVT (Network Virtual Terminal) format helps in sending commands. Then, receiving and interpreting these commands are done by the server and sent to the appropriate application.
In contrast, SSH provides you with a secure connection to the server through port 22 (note that you can change the port number). As you may know, SSH uses key-based authentication; so after the client verifies the server, a session key is generated and sent to both client and the server. This key encrypts the traffic for that session. Finally, the server verifies the client using an SSH key pair generated, completing the client authentication process. By going through these steps, we established an encrypted connection, and the two systems securely can exchange data.
Telnet vs SSH: Security
Telnet doesn’t use any security protocols during sending data, which causes it to be highly vulnerable. So, Unless we use Telnet on private and trusted networks, it is unsafe to utilize this protocol. On the contrary, SSH sessions utilize paired keys for authentication; as you can gather, this approach makes it extremely hard to decrypt and read the exchanged data. So SSH counts as a highly secure way of transferring data over unsecured networks.
- [SSH]
Telnet vs SSH: Authentication
Telnet has no authentication mechanisms for establishing a connection. However, SSH takes advantage of public-key encryption as the most common and secure SSH authentication. After SSH key pair Generation, the client keeps the private key. In the meantime, the public key is sent to a server. If a client tries to access a server using SSH, the server authenticates that client by comparing the public key to the private key. If the keys match, then two systems can establish a secure connection.
Telnet vs SSH: Data Format
Telnet can only transfer data as plain text using the Network Virtual Terminal format; however, SSH can encrypt traffic in both directions. Not only does SSH use an Encrypted format to send data, but it also uses a secure channel to do it.
Telnet vs SSH: Use cases
Considering that SSH is much more secure than Telnet, it is helpful for almost all use cases, particularly for public networks. Compared to Telnet, SSH also offers more functionality, such as secure file transfer and port forwarding. However, there are two cases in which using Telnet over SSH is recommended:
- When working on trusted and private networks, such as LANs, you can use Telnet
- When using devices that can’t support SSH
In these situations, Telnet’s lack of security stops being an issue, and at the same time, the lower bandwidth usage counts as a benefit. In this section of the article, we compared Telnet vs. SSH from different angles. In the next paragraph, you will get familiar with their main advantages and disadvantages.
What are the advantages and disadvantages of Telnet?
In what follows, we listed some benefits and drawbacks of Telnet.
Advantages of Telnet✅
- Telnet protocol can be useful for sending and receiving information without any problem.
- All terminal network clients and servers implement a network virtual terminal (NVT).
- Telnet can be used in almost all types of operating systems.
- You don’t have to physically go to any host, so this protocol can save a lot of time.
- Telnet is very flexible, meaning that you can deploy it on any system without complications.
Disadvantages of Telnet🚫
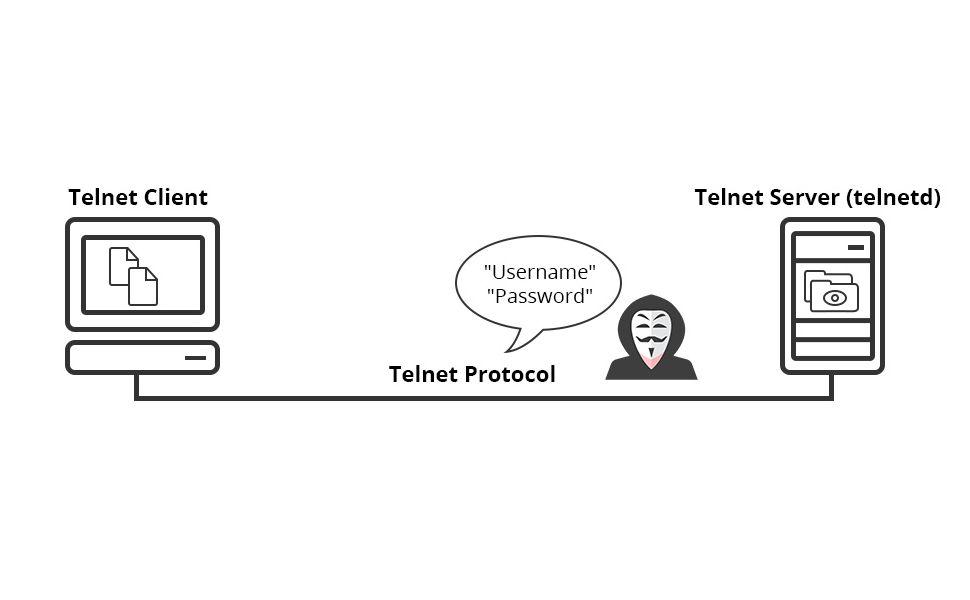
- Telnet’s unencrypted data exchange can lead to security risks.
- You can’t run GUI-based tools over Telnet connection, as it is a character-based communication tool. In addition, transmitting cursor movements and other GUI information is not possible.
- Telnet’s lack of security allows hackers to access data, such as usernames and passwords.
- [attackers-stealing-user-pass]
As we stated in this section, using Telnet can cause many flaws, which is why Secure Shell emerged in the mid-1990s to guarantee safety and security.
What are the advantages and disadvantages of SSH?
Of course, SSH is more secure than Telnet; However, SSH has its pros and cons.
Advantages of SSH✅
SSH allows data encryption so that hackers and attackers cannot access user information and passwords. Additionally, SSH also permits the tunneling of other protocols like FTP. Below we will point out various issues from which SSH can protect you:
- IP source routing
Source routing often is used for good purposes, such as altering the path of a network signal. But if it fails, it could also be manipulated by malicious users, making a machine assume that it is talking to a different one.
- DNS Spoofing
DNS Spoofing is a hacking attack in which they insert corrupt Domain Name System data into the server’s cache database. This DNS cache poisoning causes the name server to return an incorrect IP address, diverting traffic to another computer. Attackers can use their computers to obtain sensitive information.
- Data manipulation
Along with the network route, the attacker can obtain or change data at intermediaries. This issue often occurs at routers where data enters a sort of gateway or checkpoint on the way to its destination.
- Eavesdropping or sniffing transmitted data
If you are using an unsecured connection, an attacker can monitor the data and collect all sensitive or private information for their malicious benefits.
- IP address spoofing
IP address spoofing means creating Internet Protocol (IP) packets with a false source IP address. This way, the source’s identity and location are kept secret so that the attacker can impersonate using another computing system.
Disadvantages of SSH🚫
- Extra upfront work compared to Telnet.
- SSH has no native GUI.
- Using SSH Requires more technical knowledge.
Now that you read about comparing Telnet vs. SSH, you can also read this article to introduce the best SSH client for Windows. Another question might come to your mind. How do we configure a line on a router or a terminal server?
What is transport input Telnet SSH?
The virtual terminal (VTY) lines allow you to remotely access devices. You can use the Cisco “transport input” command to specify which protocols are allowed to access the virtual terminal lines. To do so, You can write the following transport input command keywords to set the allowed protocols on the VTY lines:
- ssh: allows TCP/IP SSH protocol only
- telnet: allows TCP/IP Telnet protocol only
- all: allows all protocols
- none: blocks all protocols
- telnet ssh: allows both Telnet and SSH protocols
Other Telnet commands
Some of Telnet commands are listed here:
- Open: Opening the hostname port number to establish a Telnet connection to a host.
- Close: Helps to close an existing Telnet connection
- Quit: to exit from Telnet
- Status: determining whether the Telnet client is connected or not.
- Timing Mark: defines the timing marks.
- Terminal Type/Speed: Setting the terminal type and speed
Other SSH Commands
Here are some useful SSH commands:
- ls: Show directory contents
- cd: helping to change the directory
- mkdir: to create a new folder (directory)
- touch: allowing you to remove a file
Nowadays, Remote Connection to server infrastructure is a daily occurrence at IT and DevOps organizations. But when you want to choose an authentication protocol to use, there are a few worthy choices to consider. Two protocols that come into mind are the Windows Remote Desktop Protocol (RDP) and SSH protocol.
In previous sections of this article, we explained Telnet vs. SSH comparisons from various aspects. Now, here is a comparison of RDP vs. SSH so that you can choose wisely. But before diving into comparing these two protocols, do you know what RDP is?
 Need a Remote Desktop?
Need a Remote Desktop?
Reliable, high-performance RDP servers with 99.95 uptime. Take your desktop on the go to all the major cities in the US, Europe, and Asia.
Get an RDP ServerWhat is RDP?
The Remote Desktop Protocol is only designed to access Windows virtual machines (VMs) and physical Windows servers. From your perspective, as a user, RDP can provide a Windows Graphical User Interface (GUI) experience, which makes servers more accessible to many employees, even without a technical background. In this regard, we are proud to offer our client the most reliable, high-performance RDP servers with 99.95 uptime. You can easily compare the best RDP Servers by clicking on the link below.
 Free Windows 8
Free Windows 8
If you need Windows 8 to run special software or an efficient remote desktop, Cloudzy Windows 8 VPS is for you.
Get Windows 8 VPSConclusion
Telnet and SSH are both network protocols that can help you access and manage devices remotely. While SSH protocol is the better option, Telnet is still useful in some situations. It is important to remember that the main difference between Telnet and SSH is that SSH encrypts traffic in both directions, all data, including usernames and passwords. Additionally, as far as GUI experience is concerned, the alternative is to buy RDP. using RDP provides you with a graphical interface to connect to another computer over a network connection.
FAQ
Why did SSH replace Telnet?
SSH provides a secure alternative to Telnet. This protocol can protect user identities, passwords, and data from snooping attacks.
Is Telnet a security risk?
Credential information (usernames and passwords) submitted through Telnet is not encrypted, making them vulnerable to identity theft.
Is Telnet faster than SSH?
Telnet protocol is faster; because it doesn’t involve key exchange and encryption.
What is the difference between SSH and RDP?
Both are used to remotely access machines and other servers, but the GUI-focused RDP makes it widely accessible, even by non-technical employees.