Unauthorized access and hacking servers are serious threats, which is why you should implement a firewall as part of your network security technique. Knowing how to work with Iptables rules is one of the primary assets to decrease these risks on your Linux systems. This tutorial will guide you to get familiar with basic firewall concepts such as iptables show rules and remove iptables rules in Ubuntu, helping you run simple commands to achieve this. Before discussing how to list iptables rules or delete them, let’s talk about what iptables rules are and why we use them?
What is Iptables?
iptables is a command-line firewall utility that allows or blocks traffic via policy chains. When connections try to be made on your system, iptables looks for a rule in the list that matches them, giving you a proper assistant in network security. If it doesn’t find one for a connection, it resorts to the default action.
iptables almost always come pre-installed on any Linux distribution. You can use the following command to update or install it:
sudo apt-get install iptables
Why do we use Iptables?
As a Linux command line firewall, iptables allows system administrators to handle incoming and outgoing traffic via configurable table rules. Iptables use a set of tables with chains containing a set of built-in or user-defined rules.
As mentioned in the previous section, iptables plays an essential role in network security for most Linux systems. The rest of this article is mainly focused on describing iptables list all rules, including concepts like how to show iptables and remove iptables rules.
More specifically, this article will discuss some of the essential iptables tasks to show you how to List rules, delete packet and byte counters, Remove Iptables rule, Flush chains, and delete all chains & accept all traffic.
A complete guide to Iptables in Ubuntu
Before going through iptables show rules, note that you must be using a Linux server with the iptables command installed. In addition to these requirements, it is essential to have sudo privileges. When working with firewalls, pay attention not to lock yourself out of your server by blocking SSH traffic (port:22, by default). If you lose access because of your firewall settings, you may need to connect to it via an out-of-band console to fix it.
Also Read: How to Change the SSH Port in Linux | A Quick Step-by-Step Guide to Your SSH Port
Listing Rules by Specification
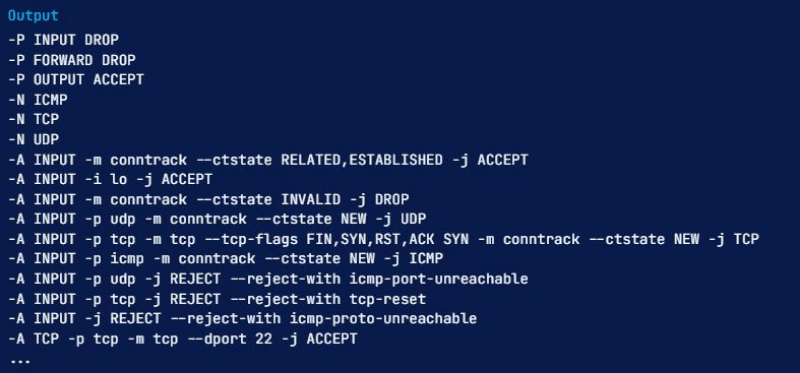
You can view your active iptables rules in a table or as a list of rule specifications. Almost both methods provide the same information in different formats. To list all rules of the active iptables by specification, you need to run the iptables command with the -S option:
sudo iptables -S
After running this iptables show rules command, you will see an output like this:
Listing a Specific Chain
If you want to limit the output of show iptables to a specific chain like INPUT, OUTPUT, or TCP, you can specify the chain name directly after the -S option. For example, the following iptables show rules command helps specify in the TCP chain:
sudo iptables -S TCP

As we referred to before, there is another way to get iptables show rules accomplished: viewing iptables rules as a table of rules. Let’s go through this technique.
Listing Rules as Tables
Using a command to show iptables rules in the tables can help compare various rules. You need to run the following show iptables command with the -L option to output all of these active rules in a table:
sudo iptables -L
This command will display all of the current rules sorted by chains. There is a way for you to limit the output to a specific chain such as INPUT, OUTPUT, TCP, etc.; you need to specify the chain name directly after the -L option. Here is an example of limiting iptables show rules to the INPUT chain:
sudo iptables -L INPUT
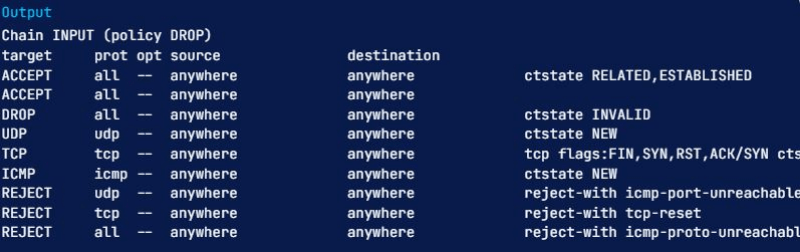
The first line of the above output shows the chain name (INPUT, in this case) and its default policy (DROP). The following line contains the headers of each column in the table and the chain’s rules. We will go through them to help you learn them all:
- Target: If a packet corresponds to the rule, the target determines what should be done with it. You can have a packet accepted, dropped, logged, or sent to another chain to be compared against more rules.
- prot: The protocol (like TCP, udp, ICMP, or all)
- opt: indicates IP options (Infrequently used)
- source: shows the source IP address/subnet of the traffic
- destination: presents destination IP address/subnet of the traffic
The column with no label suggests a rule’s options, and it is any part of the rule that has not been indicated in the previous columns. This info can be anything, from source and destination ports to the packet’s connection state.
How to show packet counts and aggregate size?
When listing iptables rules, we can show the number of packets and the aggregate size of the packets in bytes that match each particular iptables rule; this is often helpful in understanding which rules match against packets. You have to use the -L and -v options together to accomplish this.
Here is an example in which we will be using the INPUT chain again, with the -v option:
sudo iptables -L INPUT -v
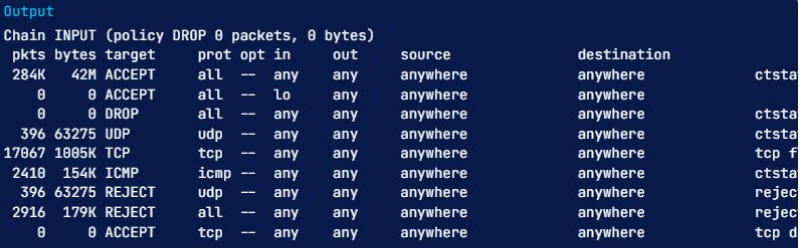
Notice that our list now has two more columns named pkts and bytes. We have learned various ways to get the iptables show all rules commands done, and it is now time to know how to reset packet counts and aggregate size.
How to reset packet counts and aggregate size?
You must use the- Z option if you like clear or zero packet and byte counters for your rules. They also reset if a reboot occurs, which is helpful if you want to see whether the server is receiving new traffic matching your existing rules.
You can clear the counters for all chains and rules using the -Z option by itself:
sudo iptables -Z
To remove the counters for all rules in a specific chain, you must use the -Z option and specify the chain. For instance, the following command is used to clear the INPUT chain counters:
sudo iptables -Z INPUT
If you want to remove the counters for a specific rule, you must mention the chain name and rule number precisely. For instance, you can execute the following command to zero the counters for the first rule in the INPUT chain:
sudo iptables -Z INPUT 1
In addition to knowing the iptables show all rules commands and ways to reset the iptables packet and byte counters, it is good to know how to remove iptables rule.
Also Read: How to Install PPTP VPN Server on Your VPS
How to Remove iptables rules?
You can use multiple commands to remove Iptables rules or even delete all rules in a chain. Here we will discuss these methods,
Remove Rules by Specification
One of the ways to remove iptables rules is doing it via rule specification. It enables you to run the iptables command with the -D option and the rule specification. If you want to remove rules using this technique, you can utilize the output of the rules list, iptables -S, for help.
For instance, to delete the rule that drops invalid incoming packets (-A INPUT -m conntrack –ctstate INVALID -j DROP), you can execute the following command-line:
sudo iptables -D INPUT -m conntrack --ctstate INVALID -j DROP
Pay attention that the -A option is for indicating the rule position at creation time and should be excluded here.
Remove rules by chain and number
The other method you can use to remove iptables rules is via its chain and line number. Type the following command to choose a rule’s line number, list the rules in the table format, and add the –line-numbers option:
sudo iptables -L --line-numbers
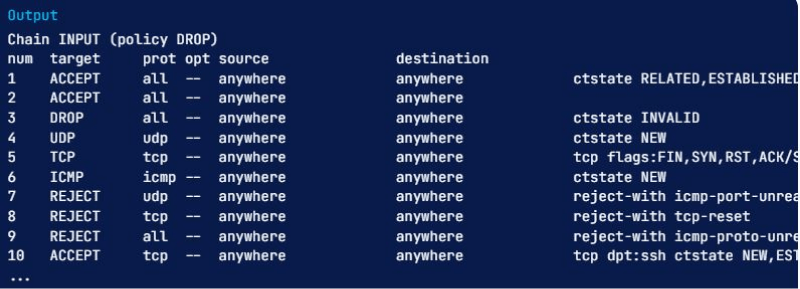
After running this, all iptables rules have their line number, shown by the num header.
When you know which rule you would like to delete, have its chain and line number in your mind. You must use the iptables -D command with the chain and rule number. For example, if you want to delete the input rule that drops invalid packets, you can see that it’s rule 3 of the INPUT chain. So run this command:
sudo iptables -D INPUT 3
How to flush chains?
There is a way for you to remove all Iptables rules in a chain, which we call flushing a chain. Here we will cover the various methods to do this. Before going any further, pay attention not to get locked out of the server via SSH when flushing a chain with a default policy of drop or deny. Because If you do, you may need to connect to it via the console to fix your access.
Flush a Single Chain
For flushing a specific chain or, in other words, deleting all of the rules in the chain, you can use the -F or the equivalent –flush option and the name of the selected chain. Say you want to remove all of the rules in the INPUT chain; what to do? Well, it is easy, run the following command:
sudo iptables -F INPUT
Flush All Chains
To Remove all chains or flush them, you can use the -F or the equivalent –flush option by itself:
sudo iptables -F
How to Flush All Rules, Delete All Chains, and Accept All?
At this point, we will describe how to flush all firewall rules, tables, and chains and permit all network traffic. Please pay attention that this process will effectively disable the firewall. So, You should only follow this section if you want to start over with your firewall configuration.
You first need to set the default policies for each of the built-in chains to ACCEPT. The primary cause we do this is to make sure that you will not be locked out from server with SSH:
sudo iptables -P INPUT ACCEPT
sudo iptables -P FORWARD ACCEPT
sudo iptables -P OUTPUT ACCEPT
Then you need to flush the nat and mangle tables, flush all chains (-F), and delete all non-default chains (-X) like this:
sudo iptables -t nat -F
sudo iptables -t mangle -F
sudo iptables -F
sudo iptables -X
After running the previous commands, the firewall will allow all network traffic. If you want to list your rules now, you will see there are none; only the three default chains such as INPUT, FORWARD, and OUTPUT chains remain.
How to set iptables in Ubuntu?
As with any basic firewall behavior, the iptables rules can be read by the order listed on each chain, which means you will have to set the rules in the correct ordering. Once you append new rules, you will have them added to the end of the rule list. You can add new rules to a particular list position by inserting them using iptables -I <index> -command. The <index> is for the order number you wish to insert the rule in this command. You can use the following command to understand which index number to enter:
sudo iptables -L --line-numbers
The number at the start of each rule line shows the position in the chain. To add a new rule above a specific existing rule, you must use the index number of that existing rule. For instance, if you like to add a new rule to the top of the chain, you have to use the following command with index number 1:
sudo iptables -I INPUT 1 -p tcp --dport 80 -j ACCEPT
How does iptables differ from firewalld?
Both iptables and firewalld are practical tools for managing firewalls on various Linux systems explicitly designed for packet filtering (static filtering). Packet filtering is a firewall strategy that enables users to control access to a specific network via managing incoming and outgoing information packets. They either allow them to pass through or deny them based on pre-set firewall rules about their source and destination protocols and ports and IP addresses. These rules provide very efficient security mechanisms, making information packet filtering a great defense against devices routed outside the system LAN (Local Area Network).
Note that firewalld was initially introduced as software to handle iptables to help make it easier for the user to navigate it. Having this introduction of firewalld and iptables, let’s compare them in more detail.
iptables vs firewalld: System configuration
Firewalld and iptables utilize different configurations and default storage settings. With iptables, every change means flushing out all the old rules and reading the new ones, so the system has to reboot. However, using firewalld, the rules are not re-created; instead, the dissimilarities and modifications made are applied to alter the existing rules so that you can see them taking effect in the runtime.
iptables vs firewalld: User interface
Firewalld uses a Graphic User interface (GUI). Yet, iptables utilizes a Command Line Interface (CLI), which may be challenging for some people to access the Linux kernel firewall rules using iptables, making firewalld a more straightforward option. It would be best to consider that iptables have a shorter response time as you only use short commands. All these aside, both have their use-cases, so pick the one you are more comfortable working with.
Final thoughts: iptables show rules
Iptables is a highly flexible firewall utility specifically created for Linux operating systems. It does not matter if you’re a newcomer Linux geek or a professional system administrator; there’s some way that iptables rules can be helpful to you. This article mainly represented basic commands for this firewall utility, including iptables show rules and remove iptables rules, aiming to briefly review Linux capabilities. Additionally, you can use our Linux VPS hosting solutions to utilize the true potential of this fantastic operating system. At cloudzy, we offer various KVM-powered Linux VPS plans suitable for multiple use-cases, such as web hosting, deploying a web app, or even setting up an environment to develop, test, and automate code.
FAQ
How to list all Linux iptables rules by specification?
If you want to list all the currently active iptables rules by their specification or functionality, you can do so by iptables command followed by the -S flag. Pay attention to utilizing the sudo keyword in this case:
sudo iptables -S
How to remove iptables rules?
To remove a specific chain, which will delete all of the rules in the chain, you must use the -F or –flush option and the name of the chain. Say we want to delete all of the rules in the OUTPUT chain, what to do? Well, you need to execute this command:
sudo iptables -F OUTPUT
How do iptables work in Ubuntu?
The iptables firewall compares network traffic against a set of rules. The iptables rules specify the characteristics of a packet to match the rule and what action should be taken if packets match. Of course, there are many options to set which packets match a specific rule.
Do iptables rules take effect immediately? Why?
Yes, iptables rules take effect instantly; because your script is appending to the INPUT and OUTPUT chains, and your rules are being added to the end of those chains.





One thought on “Listing and Deleting Linux Iptables Rules – A Cheat Sheet For Beginners”
Greetings! This is my 1st comment here so I just wanted to give a
quick shout out and tell you I really enjoy reading your blog posts.
Can you recommend any other blogs/websites/forums that deal with the same topics?
Appreciate it!