Netcat is a versatile utility that reads and writes data across
network connections using the TCP/IP protocol. It’s a valuable tool for
network debugging and exploration, and it’s also used in various
security activities like port scanning, transferring files, and creating
a backdoor during penetration testing. This article provides a
step-by-step guide on installing and using Netcat’s listening feature on
Ubuntu or Debian systems.
Installation of
Netcat
Netcat is a standard utility available in the repositories of most
Linux distributions. Below are the installation instructions for some of
the most common Linux distributions.
nc -h
Ubuntu/Debian
On Ubuntu or Debian, you can install Netcat using the following
commands:
sudo apt-get update
sudo apt-get install netcatCentOS/RHEL
For CentOS or Red Hat Enterprise Linux, you can use YUM (or DNF on
newer versions) to install Netcat:
sudo yum install ncUsing Netcat
Listener
The Netcat listener function allows you to monitor network traffic on
specific ports, providing real-time insights into data transmission and
aiding in network troubleshooting or security analysis.
Part 1: Scanning for
Open Ports
Before setting up a listener, it’s useful to identify open ports on
your server. Netcat can scan a single port or a range of ports.
Scanning a Range of Ports:
To scan a range of ports, use the following command, replacing
[REMOTE_COMPUTER_IP] with the server’s IP address and
[PORT_RANGE] with the range of ports to scan, such as
2000-5000:
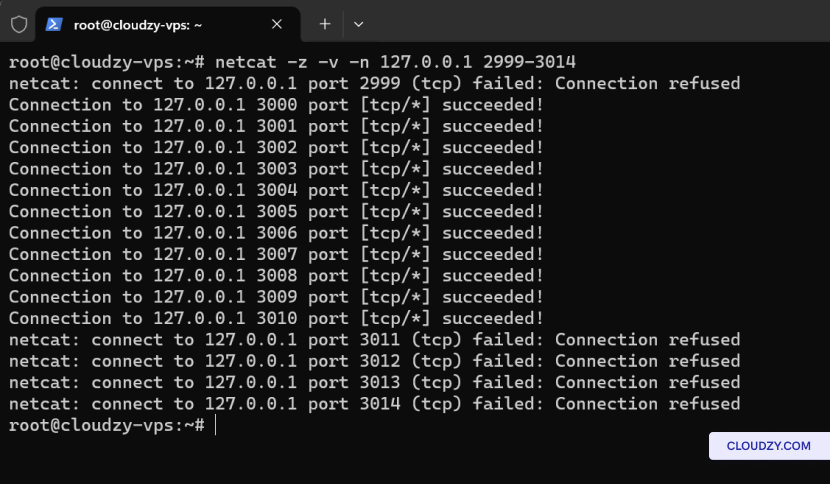
netcat -z -v -n [REMOTE_COMPUTER_IP] [PORT_RANGE]Example:
To scan ports ranging from 2999 to 3014 on a server with IP
127.0.0.1, the command would be:
To filter out the results and display only the open ports, you can
use grep:
netcat -z -v -n 172.86.74.34 2000-5000 2>&1 | grep succeeded!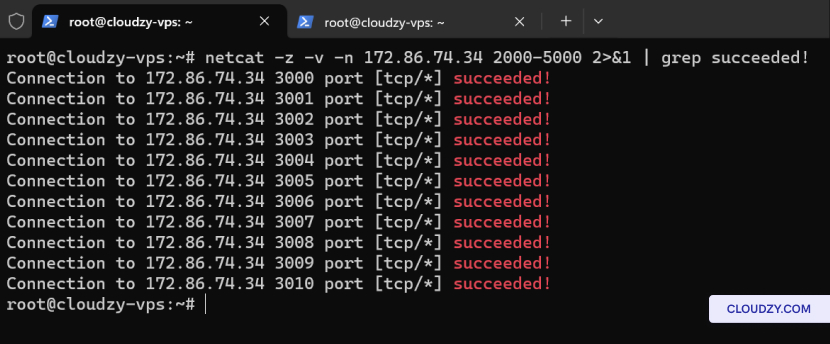
Scanning a Single Port:
If you need to check a single port, you can use:
netcat -z -v -n [REMOTE_COMPUTER_IP] [PORT]For example, to scan port 3000 on the server:
netcat -z -v -n 172.86.74.34 3000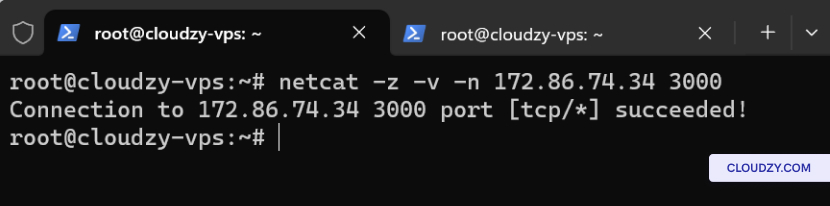
This command will indicate whether port 3000 is open or closed.
Part 2: Setting Up
a Netcat Listener
Once you’ve identified an open port or if you have a specific port
you want to monitor, you can set up a Netcat listener. To listen on port
2200, for instance, use the following command:
netcat -l -p 2200
This command will instruct Netcat to listen on port 2200 for any
incoming data.
Part 3: Sending a Test
Message
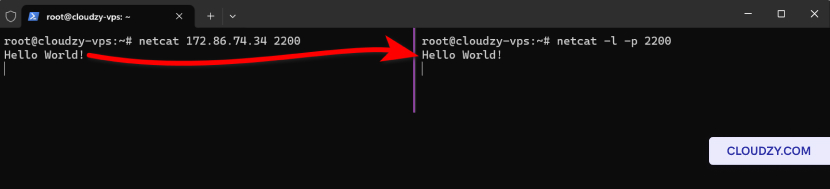
To verify that your Netcat listener is properly set up, you can send
a test message from another machine. Open a terminal on another computer
and use the following command:
netcat [SERVER_IP] 2200Replace [SERVER_IP] with the IP address of the
server where the Netcat listener is running. Once the connection is
established, you can type your message and press Enter. The message
should appear on the server where the Netcat listener is set up.
Part 4: Saving Data to a
File
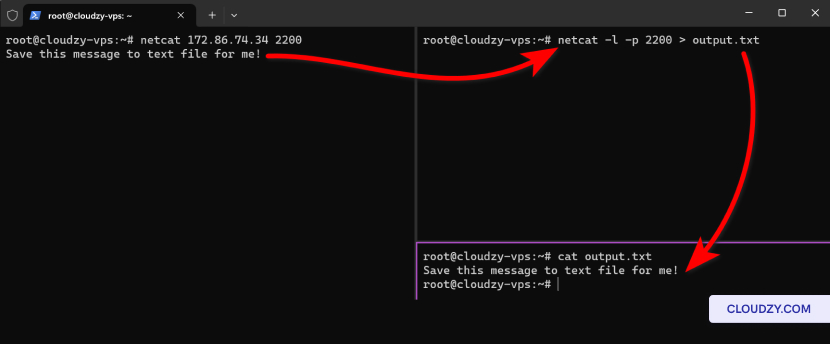
If you want to keep a record of the data passing through the port
you’re monitoring with Netcat, you can redirect the output to a file.
Here’s how to save the incoming data to a file named
output.txt:
netcat -l -p 2200 > output.txtExecuting this command will direct anything received by the Netcat
listener on port 2200 to the file
output.txt You can later review this file with any text
editor.
Part 5: Sending a
File
To send a file using Netcat, you’ll need to perform actions on both
the sending and receiving machines.
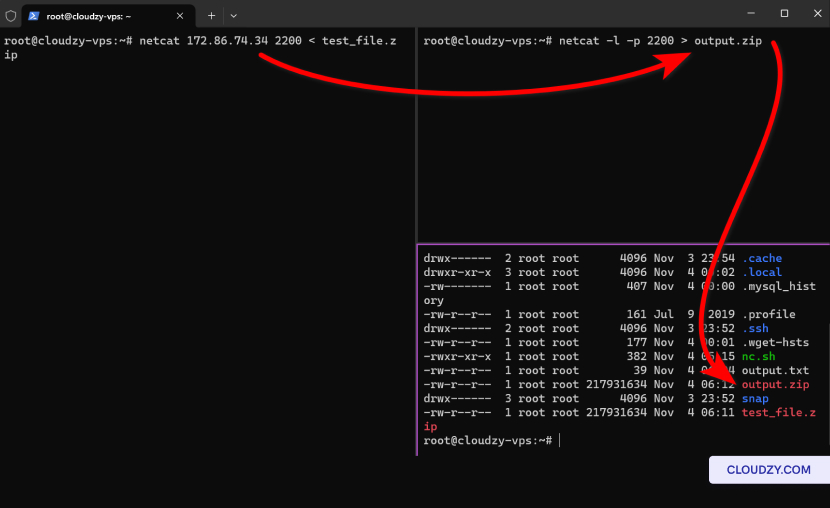
On the Receiving Machine:
Set up Netcat to listen on a specific port and redirect the incoming
data to a file. For example, to listen on port 2200 and save the
incoming data to output.zip, use:
netcat -l -p 2200 > archive.zipOn the Sending Machine:
Send a file using Netcat by connecting to the listener’s IP address
and port, then redirecting the file into Netcat. Replace
[RECEIVER_IP] with the IP address of the receiving
machine:
netcat [RECEIVER_IP] 2200 < yourfile.zipReplace yourfile.zip with the path and name of the
zip file you wish to send.
Note: When transferring files, ensure that there is
no firewall blocking the connection and that the receiving machine’s
Netcat process is initiated before the sending command is executed.
Additional
Capabilities of Netcat
Netcat’s versatility extends far beyond simple file transfers and
port listening. It’s a multifaceted tool that serves various
network-related purposes, from security to communication. Here’s a
glimpse into its additional capabilities:
-
Chat Server Creation: Netcat can be configured
to facilitate real-time text communication between users, acting as a
rudimentary chat server. -
Service Banner Grabbing: By connecting to open
ports, Netcat can retrieve service banners, aiding in the identification
of potentially vulnerable software versions. -
Network Debugging: It’s an excellent tool for
diagnosing network services, allowing you to send custom requests and
analyze the responses for troubleshooting. -
Remote Administration: Netcat can bind a shell
to a network port, enabling remote command-line access to another
computer, which is particularly useful for system
administrators. -
Network Daemon Testing: Developers can use
Netcat to interact with network daemons, sending test data and commands
to see how the service behaves. -
Proxy Server Functionality: With Netcat, setting
up a basic proxy is straightforward, allowing you to forward traffic and
potentially monitor or analyze it for various purposes. -
Network Service Emulation: It can simulate
network services, providing a mock response to incoming network
requests, which is useful for testing client-side applications. -
Basic TCP/UDP Server Setup: Netcat can listen on
specified ports for incoming TCP or UDP requests, making it a tool for
creating simple servers. -
Scripting and Automation: Its command-line
nature allows Netcat to be easily scripted and integrated into larger
automation tasks, streamlining repetitive network operations. -
Data Tunneling: Netcat can be used to create a
data tunnel, allowing for the redirection of data streams from one
network to another. -
Time Synchronization: It can facilitate the
synchronization of system clocks across a network by sending time data
between machines. -
Security Testing: Netcat is a staple in security
testing, used to simulate network attacks or test the effectiveness of
firewall configurations. -
Connection Testing: Quickly and efficiently test
the ability to establish TCP or UDP connections, which is essential for
network setup and maintenance.
Each of these capabilities highlights the adaptability of Netcat,
making it an indispensable tool in the networking toolkit. Whether for
development, troubleshooting, or security analysis, Netcat’s simplicity
and power make it the go-to utility for network professionals. If you
have any questions, feel free to contact us by submitting a
ticket.