SSH (Secure Shell) is an important aspect of secure network
administration and provides a secure method to access remote servers.
Authentication within SSH is a multi-faceted process that involves
methods like password, public key, and multi-factor authentication (MFA)
to verify user identity. Understanding these authentication methods and
their common issues is essential for secure and effective remote server
access.
Prerequisites
-
Administrative access to the server to manage SSH configurations
and user accounts. -
Familiarity with SSH key generation and the setup process for
public and private keys. -
Understanding of the server’s password policy and account
management procedures. -
Knowledge of configuring and troubleshooting MFA setups.
-
Access to the server’s SSH configuration files, typically located
at /etc/ssh/sshd_config. -
Ability to use command-line tools for log analysis and
configuration file editing. -
For SSH agent issues, understanding how SSH agents work and how
to add keys to the agent.
Common SSH
Authentication Issues Explained
Password
Authentication Failures
Password issues are one of the most common SSH authentication
problems. Users may enter their passwords incorrectly can lead to
account lockouts due to security policies. Password expiration is
another aspect where passwords may no longer be valid after a certain
period.
Public Key
Authentication Problems
This form of authentication is more secure than passwords but comes
with its own challenges. If the public key is missing from the server’s
.ssh/authorized_keys file or if the private key on the
client side is not correctly configured or has incorrect permissions
(should be 600), authentication will fail. Another common issue is
format errors in the authorized_keys file, which can
occur if the key is copied incorrectly.
Multi-Factor
Authentication (MFA) Challenges
MFA provides an additional security layer that usually includes a
time-based code or a physical token. Common issues with MFA include time
drift on tokens leading to failed synchronizations, or users losing
access to their MFA device, which can lock them out of the system.
SSH Agent Issues
The SSH agent holds private keys used for public key authentication,
reducing the need to enter passwords. Problems can arise if the SSH
agent is not running or if keys are not added to the agent with
ssh-add. This can lead to repeated password prompts or
authentication failures.
Understanding these common issues and their implications is crucial
for maintaining a seamless and secure SSH environment.
Diagnosing SSH
Authentication Issues
When you have SSH authentication problems, a systematic approach can
help you in identifying the root cause:
Analyzing Error
Messages
SSH provides specific error messages that can guide you to the issue.
For instance, “Permission denied (publickey)” suggests a problem with
public key authentication, while “Access denied” might indicate a wrong
password or a locked account.
Checking Server and
Client Logs
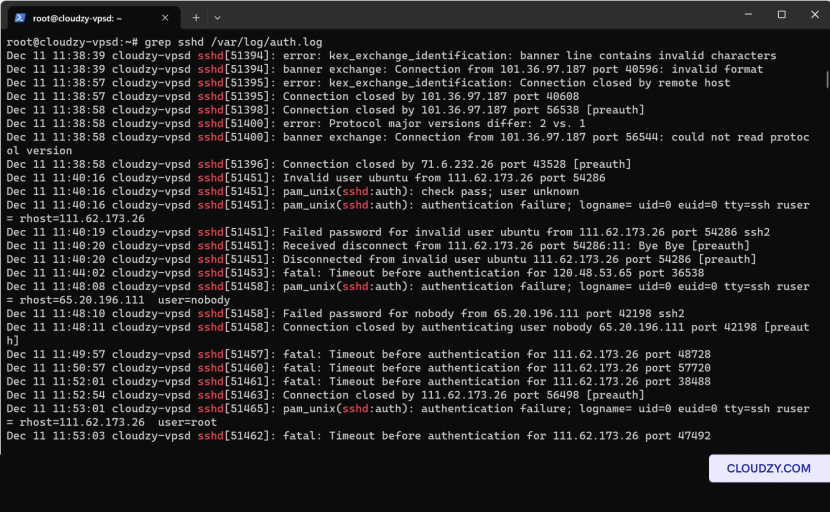
The server’s logs can provide detailed insights into authentication
failures. Use commands like grep sshd /var/log/auth.log
to filter for SSH-related log entries on the server. Similarly, check
the client logs, usually found in ~/.ssh/ or output to
the terminal, to look for clues.
Verifying
Authentication Settings
On the server, the SSH daemon configuration file at
/etc/ssh/sshd_config contains settings for
authentication methods. Make sure that password authentication, public
key authentication, and any MFA settings are correctly enabled or
disabled as required.
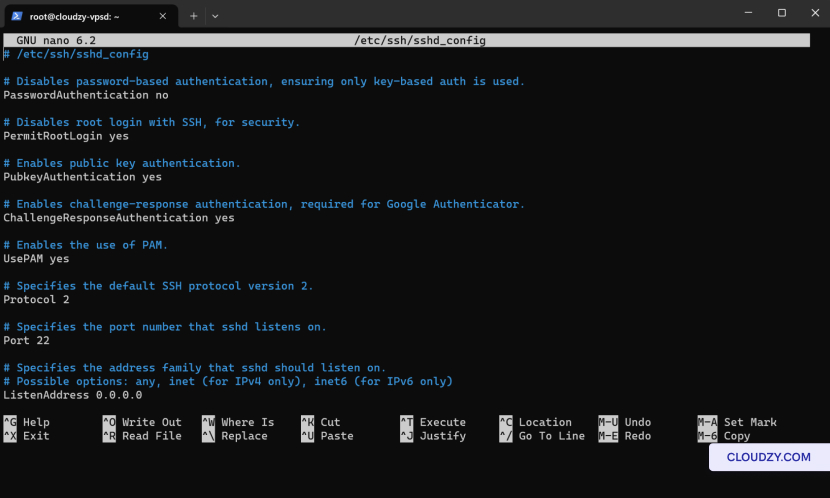
By carefully examining these areas, you can often pinpoint the exact
problem causing the SSH authentication issue.
Troubleshooting and
Solutions
Resolving Password
Issues
When you face password-related SSH authentication problems, resetting
your credentials is a straightforward process using the Cloudzy
Panel:
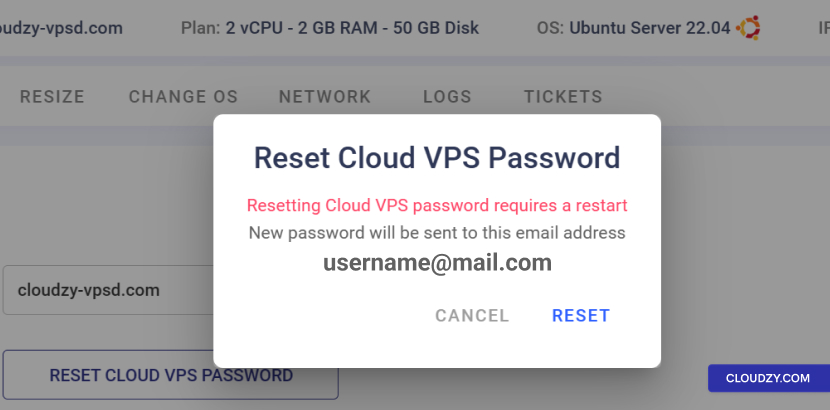
- Access Cloudzy Panel:
-
Sign in to your Cloudzy dashboard.
-
Navigate to the Access section of your specific
VPS dashboard.
- Password Reset:
-
Click on the RESET CLOUD VPS PASSWORD
button. -
A confirmation prompt will appear. Upon confirmation, the VPS
will restart, and a new password will be sent to your registered email
address.
Fixing Public Key
Authentication
Verify the public key is correctly placed in the server’s
~/.ssh/authorized_keys file. Ensure the file
permissions are correct with chmod 600
~/.ssh/authorized_keys. On the client side, check that the
private key is loaded with ssh-add -l and if not, add
it with ssh-add /path/to/private_key.
Addressing MFA
Problems
For MFA issues, ensure the server and authentication device’s time
are synchronized. If the MFA device is lost, reset MFA settings through
the server’s administrative interface, often requiring temporary
disablement of MFA for the affected account.
For issues with Google Authenticator or similar MFA tools:
-
Resync Time: Ensure the time on your server and
MFA device are synchronized. Use the ntpdate command on
the server if necessary to sync with time servers. -
Regain Access: If you have lost access to your
MFA device, use backup codes provided at setup or contact the server
administrator to temporarily disable MFA for your account to regain
access.
Managing SSH Agent Problems
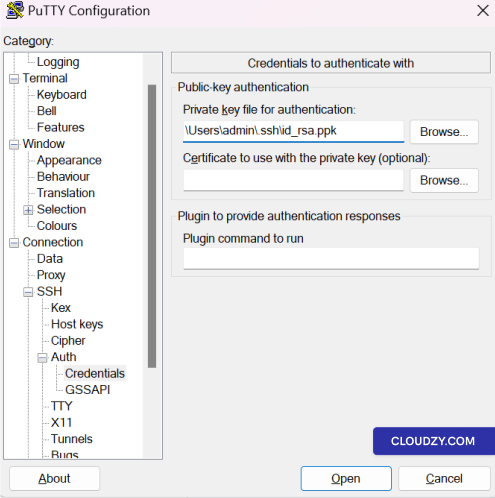
Windows with PuTTY:
-
Launch PuTTY.
-
Navigate to Connection -> SSH -> Auth -> Credentials in
the category tree. -
Click on the ‘Browse’ button to select your private key file for
authentication. This file will typically have a .ppk extension if it’s
been converted for use with PuTTY.
-
If your key file has a passphrase, you’ll be prompted to enter it
when you connect. -
Save your session settings for future use.
Windows PowerShell or Command Prompt:
- Ensure you have the ssh-agent service running:
Get-Service ssh-agent | Set-Service -StartupType Automatic
Start-Service ssh-agent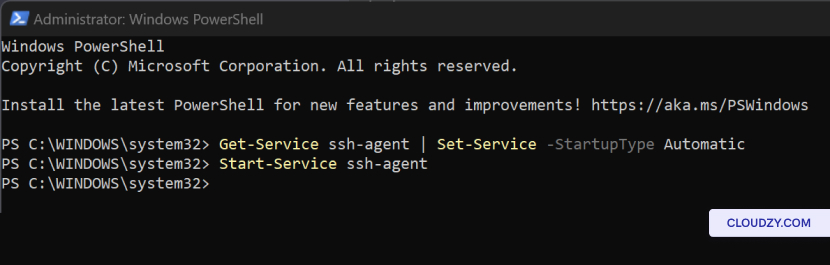
- Add your private key to the ssh-agent:
ssh-add .ssh\id_rsaReplace **.ssh_rsa** with the path to your private key file if it’s
not in the default location.
Linux Terminal:
- Start the SSH agent if it’s not already running:
eval "$(ssh-agent -s)"- Add your SSH key to the agent:
ssh-add ~/.ssh/id_rsaReplace ~/.ssh/id_rsa with the path to your private
key file if it’s not in the default location.
Remember that on Linux, ssh-add might ask for your
key’s passphrase if it has one. This is a one-time action per session or
until the agent is stopped or the system is restarted.
With these solutions, you should be able to tackle the most common
SSH authentication issues, from simple password resets to more complex
MFA and SSH agent problems. Always follow security best practices when
resolving these issues to maintain the integrity of your server’s access
protocols. If you need any more information or further assistance, feel
free to contact our support team by submitting a
ticket.